Docker网络之自定义网络方式
156人参与 • 2025-02-14 • 云虚拟主机
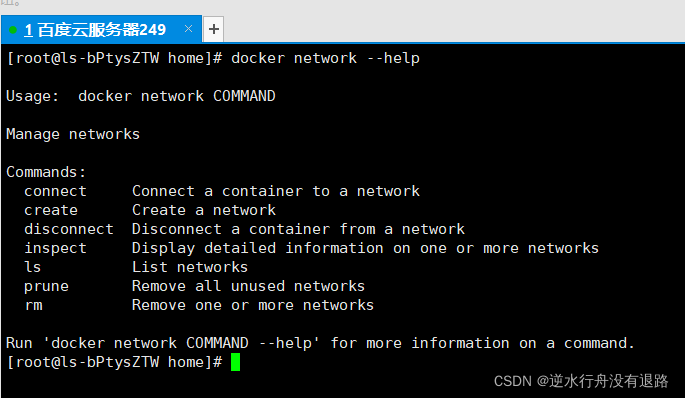
帮助命令
docker network --help
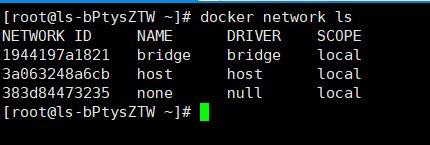
查看所有的网络
docker network ls
网络模式
| 网络模式 | 配置 | 说明 |
|---|---|---|
| bridge模式 | –net=bridge | 默认值,在docker网桥docker0上为容器创建新的网络栈 |
| none模式 | –net=none | 不配置网络,用户可以稍后进入容器,自行配置 |
| container模式 | – net=container:name/id | 容器和另外一个容器共享network namespace。kubernetes中的pod就是多个容器共享一个network namespace。 |
| host模式 | –net=host | 容器和宿主机共享network namespace |
| 用户自定义 | –net=自定义网络 | 用户自己使用network相关命令定义网络,创建容器的时候可以指定为自己定义的网络 |
查看一个网络的相信信息
[root@ls-bptysztw ~]# docker network inspect 1944197a1821
[
{
"name": "bridge",
"id": "1944197a18211b7cbd5f07b9c25f696c6fc74dfe19324b1a51db33335627c8f3",
"created": "2022-03-18t18:34:10.650916029+08:00",
"scope": "local",
"driver": "bridge",
"enableipv6": false,
"ipam": {
"driver": "default",
"options": null,
"config": [
{
"subnet": "172.17.0.0/16"
}
]
},
"internal": false,
"attachable": false,
"ingress": false,
"configfrom": {
"network": ""
},
"configonly": false,
"containers": {
"99610ffcbeb1124ac54bbb2cad77043828793028ffb75612ddbde10ce0d8ed77": {
"name": "tomcat02",
"endpointid": "da9819333b969861729adee15dae290021fddeeab91b0d878e64d4cee7efe43a",
"macaddress": "02:42:ac:11:00:03",
"ipv4address": "172.17.0.3/16",
"ipv6address": ""
},
"b4b7bcb5cf4d2c6b984400b21e2009a7936be6dec0c8db0e62f5a470c926b013": {
"name": "tomcat01",
"endpointid": "8103ffad548da7aa51eb888bae4f6b808447d49fdcb42c8b19655bddaa4b3958",
"macaddress": "02:42:ac:11:00:02",
"ipv4address": "172.17.0.2/16",
"ipv6address": ""
},
"ee86fd75423ae1d9631dfba52ea7df05904e358a35319c103e990a61e5c7904a": {
"name": "tomcat03",
"endpointid": "0f25ea01f8ec30eaa002c4e2c2346a3e249875797cf051f5c9d6de9135607d34",
"macaddress": "02:42:ac:11:00:04",
"ipv4address": "172.17.0.4/16",
"ipv6address": ""
}
},
"options": {
"com.docker.network.bridge.default_bridge": "true",
"com.docker.network.bridge.enable_icc": "true",
"com.docker.network.bridge.enable_ip_masquerade": "true",
"com.docker.network.bridge.host_binding_ipv4": "0.0.0.0",
"com.docker.network.bridge.name": "docker0",
"com.docker.network.driver.mtu": "1500"
},
"labels": {}
}
]
[root@ls-bptysztw ~]# 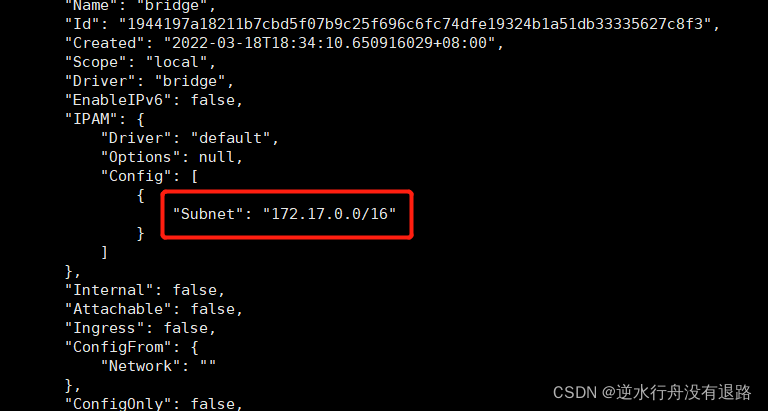
docker0子网段172.17.0.0/16,表示容器划分是0到16位,也就是意味着docker容器可以划分出65535个ip,其中172.17.0.1是网关,那么docker可以划分65534个ip提供给容器使用。
自定义网卡
1.删除所有的容器,查看网卡恢复到最开始。
docker rm -f $(docker ps -aq)
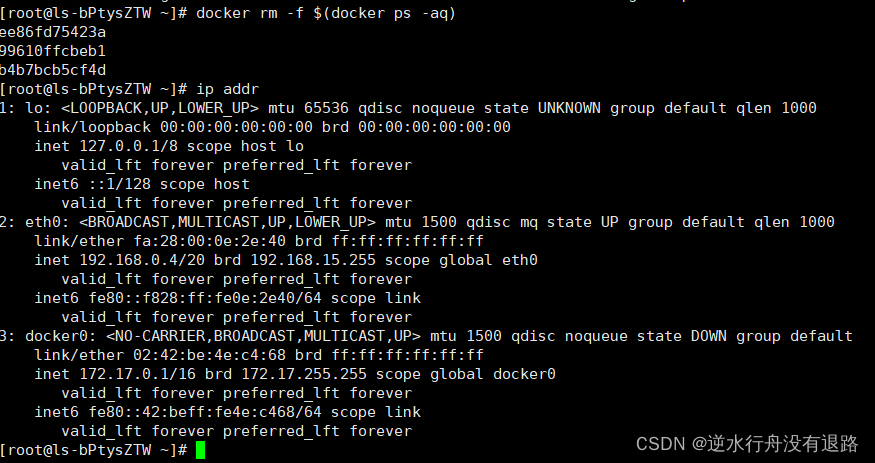
2. 接下来我们创建容器,但是我们知道默认创建的容器都是docker0的网卡。
#我们不配置网络,也叫相当于默认值,--net bridge 使用的docker0 docker run -d -p --name tomcat01 --net bridge tomcat #默认
docker0网络特点
- 他是默认的
- 域名访问不通
- –link 域名通了,但是删除了又不行
3.我们可以让容器创建的时候使用自定义网络
#自定义创建的默认default bridge #自定义创建一个网络 docker network create --driver bridge --subnet 192.168.0.0/16 --gateway 192.168.0.1 mynet
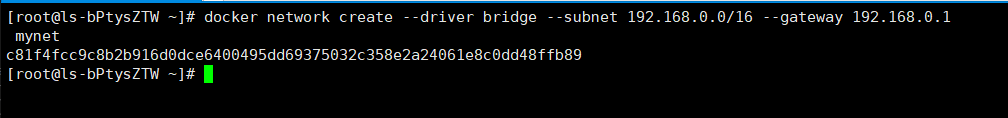
查看到我们刚刚创建的网络 docker network ls
我们来启动两个容器测试,使用自己的mynet [root@ls-bptysztw ~]# docker run -d -p --name tomcat-net-01 --net mynet lengcz/tomcat:1.0 855dc33189221c61fbe6bc35ce2b080ff71f34547ce6cf77a5c98e3afcd9daaa [root@ls-bptysztw ~]# docker run -d -p --name tomcat-net-02 --net mynet lengcz/tomcat:1.0 a8dff5c6a82649356385253c96f5ff07771644b8dca85f9a814d1b17041290df [root@ls-bptysztw ~]# docker ps container id image command created status ports names a8dff5c6a826 lengcz/tomcat:1.0 "/bin/sh -c '/usr/lo…" 20 seconds ago up 19 seconds 0.0.0.0:49158->8080/tcp, :::49158->8080/tcp tomcat-net-02 855dc3318922 lengcz/tomcat:1.0 "/bin/sh -c '/usr/lo…" 37 seconds ago up 36 seconds 0.0.0.0:49157->8080/tcp, :::49157->8080/tcp tomcat-net-01 [root@ls-bptysztw ~]#
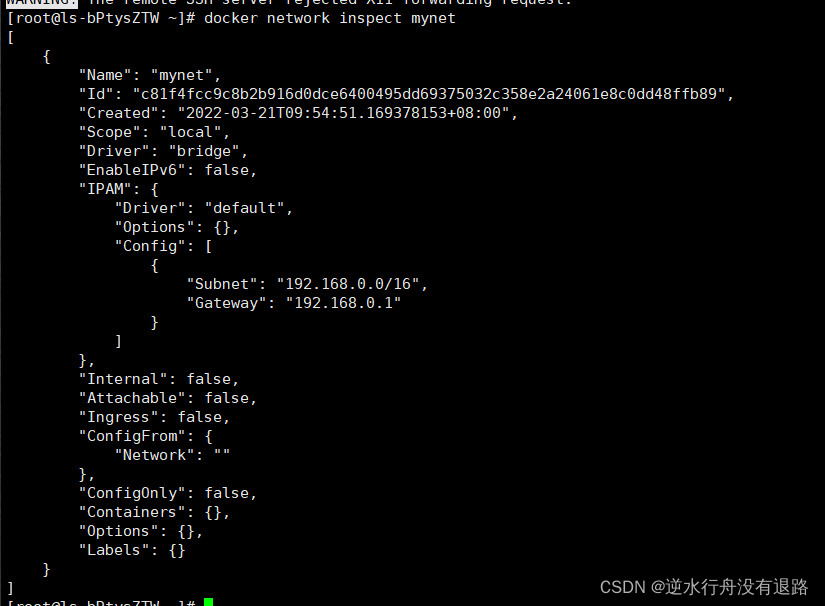
# 再次查看一下我们定义的网络,会发现containers列表里包含了两个容器的网络信息。
[root@ls-bptysztw ~]# docker network inspect mynet
[
{
"name": "mynet",
"id": "c81f4fcc9c8b2b916d0dce6400495dd69375032c358e2a24061e8c0dd48ffb89",
"created": "2022-03-21t09:54:51.169378153+08:00",
"scope": "local",
"driver": "bridge",
"enableipv6": false,
"ipam": {
"driver": "default",
"options": {},
"config": [
{
"subnet": "192.168.0.0/16",
"gateway": "192.168.0.1"
}
]
},
"internal": false,
"attachable": false,
"ingress": false,
"configfrom": {
"network": ""
},
"configonly": false,
"containers": {
"855dc33189221c61fbe6bc35ce2b080ff71f34547ce6cf77a5c98e3afcd9daaa": {
"name": "tomcat-net-01",
"endpointid": "3f5751193ffa31fa723c2a999575186e343da653e39d654c9b62a3fdf72ef8bd",
"macaddress": "02:42:c0:a8:00:02",
"ipv4address": "192.168.0.2/16",
"ipv6address": ""
},
"a8dff5c6a82649356385253c96f5ff07771644b8dca85f9a814d1b17041290df": {
"name": "tomcat-net-02",
"endpointid": "68859294c6ce5f5179390e29718982bbfd2848b6e260d0486cd33967239e4990",
"macaddress": "02:42:c0:a8:00:03",
"ipv4address": "192.168.0.3/16",
"ipv6address": ""
}
},
"options": {},
"labels": {}
}
]# 测试一下ping容器名和ip,都可以ping通 [root@ls-bptysztw ~]# docker exec -it tomcat-net-01 ping 192.168.0.3 -c4 ping 192.168.0.3 (192.168.0.3) 56(84) bytes of data. 64 bytes from 192.168.0.3: icmp_seq=1 ttl=64 time=0.099 ms 64 bytes from 192.168.0.3: icmp_seq=2 ttl=64 time=0.131 ms [root@ls-bptysztw ~]# docker exec -it tomcat-net-01 ping tomcat-net-02 -c4 ping tomcat-net-02 (192.168.0.3) 56(84) bytes of data. 64 bytes from tomcat-net-02.mynet (192.168.0.3): icmp_seq=1 ttl=64 time=0.067 ms 64 bytes from tomcat-net-02.mynet (192.168.0.3): icmp_seq=2 ttl=64 time=0.105 ms rtt min/avg/max/mdev = 0.067/0.090/0.105/0.014 ms
结论:我们自定义的网络docker已经帮我们维护好了对应的关系。所以我们平时都可以使用这样的网络,不使用–link效果一样,所有东西实时维护好,直接域名ping通。
到这里,我们基本可以理解docker网络了。
网络连通
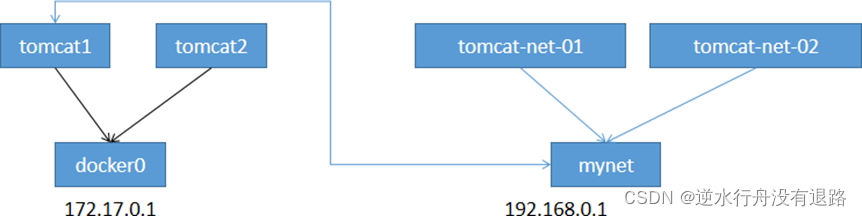
docker0和自定义网络肯定不通,我们是使用自定义网络的好处就是网络隔离:
大家公司项目部署的业务都非常多,假设我们有一个商城,我们会有订单业务(操作不同数据),会有 订单业务购物车业务(操作不同缓存)。
如果在一个网络下,有的程序猿的恶意代码就不能防止了,所 以我们就在部署的时候网络隔离,创建两个桥接网卡,比如订单业务(里面的数据库,redis,mq,全 部业务 都在order-net网络下)其他业务在其他网络。
那么关键问题来了,如何让tomcat-net-01访问tomcat01?
#启动默认的容器,在docker0网络下
[root@ls-bptysztw ~]# docker run -d -p --name tomcat01 lengcz/tomcat:1.0
a8f874ddc701eff4adf3921b65f91f1fd080bdf5c3ce429c59808249b72ca020
[root@ls-bptysztw ~]# docker run -d -p --name tomcat02 lengcz/tomcat:1.0
184e19b40cd39662e7d6d0ccf1cf440d7a455f22505a57d64636b23ea29e6945
#查看当前的容器
[root@ls-bptysztw ~]# docker ps
container id image command created status ports names
184e19b40cd3 lengcz/tomcat:1.0 "/bin/sh -c '/usr/lo…" 8 seconds ago up 7 seconds 0.0.0.0:49160->8080/tcp, :::49160->8080/tcp tomcat02
a8f874ddc701 lengcz/tomcat:1.0 "/bin/sh -c '/usr/lo…" 20 seconds ago up 19 seconds 0.0.0.0:49159->8080/tcp, :::49159->8080/tcp tomcat01
a8dff5c6a826 lengcz/tomcat:1.0 "/bin/sh -c '/usr/lo…" 3 hours ago up 3 hours 0.0.0.0:49158->8080/tcp, :::49158->8080/tcp tomcat-net-02
855dc3318922 lengcz/tomcat:1.0 "/bin/sh -c '/usr/lo…" 3 hours ago up 3 hours 0.0.0.0:49157->8080/tcp, :::49157->8080/tcp tomcat-net-01
#查看network帮助
[root@ls-bptysztw ~]# docker network --help
usage: docker network command
manage networks
commands:
connect connect a container to a network # 连接一个容器到一个网络
create create a network
disconnect disconnect a container from a network
inspect display detailed information on one or more networks
ls list networks
prune remove all unused networks
rm remove one or more networks
#测试一下!打通一下mynet-docker0
#命令docker network connect [options] network container
[root@ls-bptysztw ~]# docker network connect mynet tomcat01
[root@ls-bptysztw ~]# docker network inspect mynet
[
{
.....
"containers": {
"855dc33189221c61fbe6bc35ce2b080ff71f34547ce6cf77a5c98e3afcd9daaa": {
"name": "tomcat-net-01",
"endpointid": "3f5751193ffa31fa723c2a999575186e343da653e39d654c9b62a3fdf72ef8bd",
"macaddress": "02:42:c0:a8:00:02",
"ipv4address": "192.168.0.2/16",
"ipv6address": ""
},
"a8dff5c6a82649356385253c96f5ff07771644b8dca85f9a814d1b17041290df": {
"name": "tomcat-net-02",
"endpointid": "68859294c6ce5f5179390e29718982bbfd2848b6e260d0486cd33967239e4990",
"macaddress": "02:42:c0:a8:00:03",
"ipv4address": "192.168.0.3/16",
"ipv6address": ""
},
"a8f874ddc701eff4adf3921b65f91f1fd080bdf5c3ce429c59808249b72ca020": {
"name": "tomcat01", #发现tomcat01加入了该网络,tomcat01拥有双ip
"endpointid": "39e946d3c4b510712ab3b6dd2c921b0941e2341b914cf5e645e56e82ea725e71",
"macaddress": "02:42:c0:a8:00:04",
"ipv4address": "192.168.0.4/16",
"ipv6address": ""
}
},
"options": {},
"labels": {}
}
]
#tomcat01可以ping通了
[root@ls-bptysztw ~]# docker exec -it tomcat01 ping tomcat-net-01 -c2
ping tomcat-net-01 (192.168.0.2) 56(84) bytes of data.
64 bytes from tomcat-net-01.mynet (192.168.0.2): icmp_seq=1 ttl=64 time=0.074 ms
64 bytes from tomcat-net-01.mynet (192.168.0.2): icmp_seq=2 ttl=64 time=0.085 ms
#tomcat02依旧ping不通
[root@ls-bptysztw ~]# docker exec -it tomcat02 ping tomcat-net-01 -c2
ping: tomcat-net-01: name or service not known结论:如果要跨网络访问,就需要使用
docker network connect [options] network container 进行连接,否则就无法互相访问
最后
以上为个人经验,希望能给大家一个参考,也希望大家多多支持代码网。
您想发表意见!!点此发布评论


发表评论